In contemporary investigations, the tension between gathering critical evidence and respecting individual rights has never been more intense. This is especially true in mobile device forensics, where investigators seek to extract text messages, call logs, location data, photos, apps, and other highly personal content.
The question arises: how can we conduct investigations without trampling privacy? This blog delves deeply into mobile forensics privacy issues, exploring the ethical and legal chasms, the responsibilities of forensic professionals, and how the right protocols uphold both justice and privacy.
The Promise and Peril of Mobile Forensics
Mobile devices are ubiquitous and deeply personal. They contain treasure troves of personal data, making them prime targets in criminal investigations. On the one hand, forensic cell phone data recovery may reveal critical evidence; on the other, it threatens to expose private communications and intimate details.
Thus, mobile forensics is a double‑edged sword. Investigators and legal authorities must grapple with complex questions: When does searching a phone cross a privacy boundary? How do we authenticate video or audio evidence without overreaching? What safeguards exist to prevent abuse? Let’s explore it further.
The Legal Landscape: Search, Warrant & Fourth Amendment
The Fourth Amendment and Digital Searches
In the United States, the bedrock protection for privacy is the Fourth Amendment, which guards citizens against unreasonable searches and seizures. A mobile device is often treated as a repository of private life, so investigators generally must secure a warrant before conducting a search.
The scope of that warrant must be sufficiently specific—detailing what data or categories may be searched—so the investigator does not conduct a sweeping, privacy-intrusive search of irrelevant content.
Courts have wrestled with how to apply Fourth Amendment rules to mobile devices. Some rulings require “search incident to arrest” exceptions only when limited in scope; others require a “digital lock” warrant. The key principle is proportionality: any intrusion must be no more than necessary to achieve legitimate investigative goals.
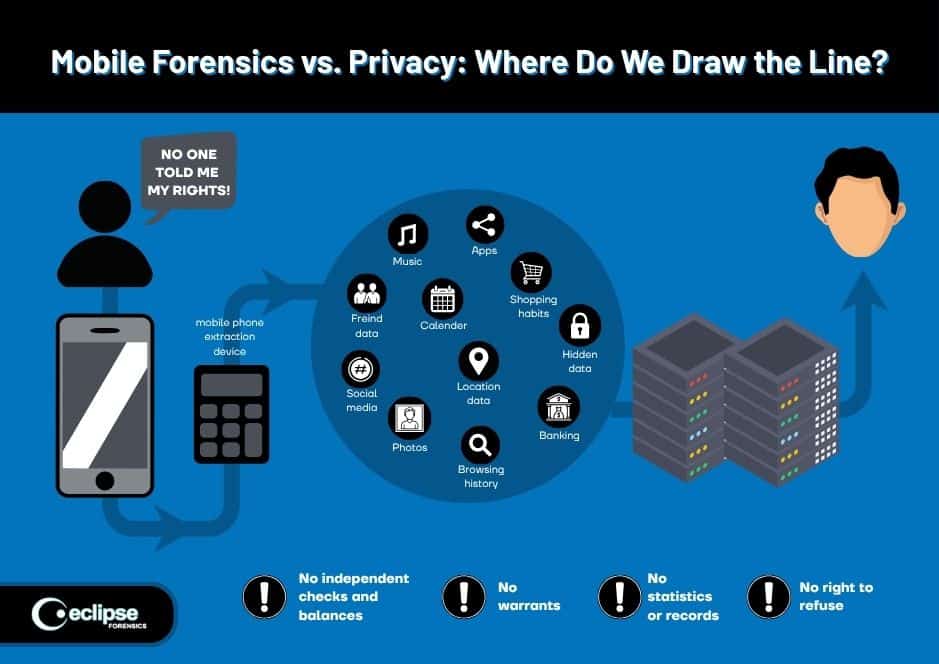
Statutes Like ECPA and SCA
Beyond constitutional protections, the Electronic Communications Privacy Act (ECPA) and Stored Communications Act (SCA) place additional constraints on accessing stored communications or data held by service providers. Investigators must tread carefully: simply obtaining a warrant may not suffice if statutory protections apply.
For example, retrieving messages stored in the cloud, tied to a phone, often implicates these laws. A digital forensic consultant must be well-versed in both constitutional and statutory regimes before engaging in extraction or requesting third‑party data.
Jurisdiction and Cross‑Border Data
Mobile data may exist across multiple jurisdictions, especially when cloud sync or remote backups are involved. A warrant issued in State A may not automatically permit the extraction of cloud‑stored data in State B or another country. That means a cyber forensic expert and data forensic expert must coordinate with legal counsel to ensure proper authority, prevent cross‑jurisdictional overreach, and respect data sovereignty.
Ethical Challenges: Scope, Relevance, and Minimization
Principle of Proportionality
Even when legal authority is obtained, forensic practitioners must remain ethically disciplined. They must continuously ask: Is the data I seek proportional to the offense? For example, in a theft case, it may be unjustified to explore a suspect’s social media chats about personal relationships. The intrusion must remain strictly tailored. That involves deploying search filters, keyword constraints, or segmented extraction methods to avoid unnecessary access.
Avoiding “Fishing Expeditions”
One of the most abused practices is the “fishing expedition” — where investigators pull more data than authorized, hoping something incriminating appears. This morally dangerous approach undermines privacy rights and can jeopardize admissibility in court. A forensic computer analyst or digital forensic engineer must resist temptation and stay within the legally permitted boundary.
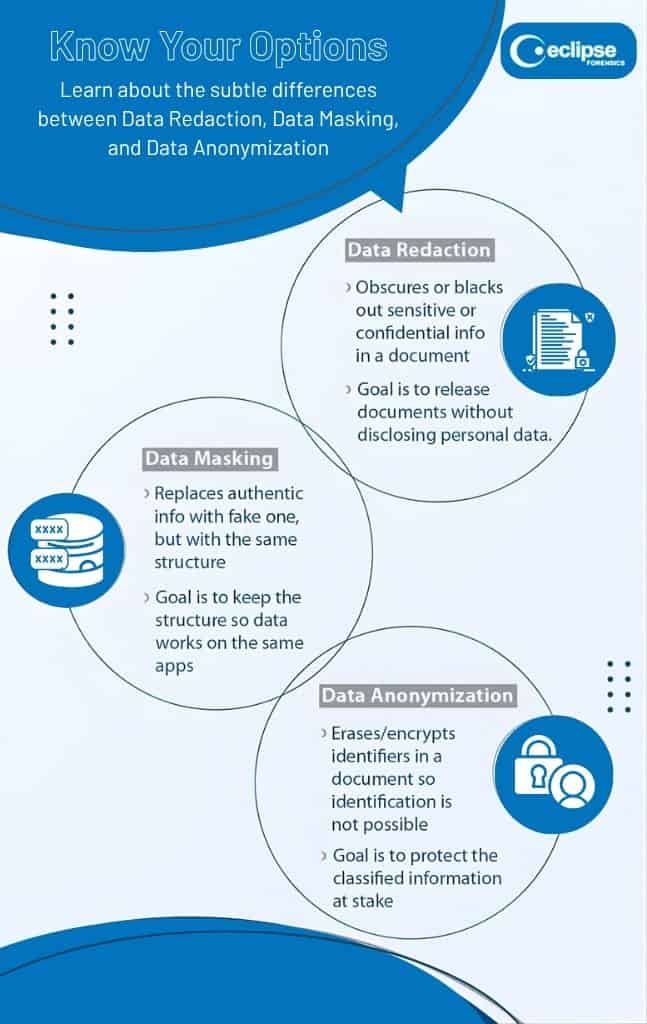
Data Minimization and Redaction
Ethical mobile forensics demands data minimization: isolating and retaining only relevant evidence while redacting or discarding extraneous personal content. For example, if certain messages or images are irrelevant, they should not be retained or disclosed. This reduces the risk of privacy violations and minimizes exposure of innocuous private details.
Transparency and Accountability
Investigators should maintain meticulous logs of their processes, demonstrating the chain of custody, extraction parameters, tool usage, and any filtering or redaction conducted. Transparency is essential both ethically and legally. A computer forensics consultant may need to produce these logs in disclosure motions or judicial review.
Technical Considerations: Encryption, Tools, and Limitations
Encryption and Access Resistance
Modern mobile devices often employ strong encryption (e.g., full-disk encryption, hardware-backed encryption). These protections are essential for user privacy but present hurdles for investigators.
Breaking encryption can require advanced technical tools, exploits, or cooperation from manufacturers—each raising its own legal and ethical implications. Should an investigator compel a suspect to unlock a device? Some courts permit it, others view it as self-incrimination. A mobile device forensics expert must stay updated on the evolving technical and legal landscape.
Forensic Tool Accuracy and Validation
Any tools used to extract or analyze data must be validated, tested, and reliably documented. Courts will demand proof that the tools preserve data integrity and do not introduce artifacts. Forensic practitioners must understand the inner workings of software and hardware to avoid misinterpretation of recovered data.
Authenticating Video and Audio
When investigators recover video or audio from mobile devices, further challenges arise. Forensic video analysis experts and video forensic experts must authenticate and analyze the content, discerning if it was edited, spliced, or manipulated. Similarly, audio forensic services must verify that recordings are genuine, untampered, and accurately represent the original. The authentication process must itself respect privacy, avoiding exposure of extraneous private parts of a recording that fall outside the investigation’s purview.

Data Integrity and Chain of Custody
A cornerstone of all forensic work is maintaining the integrity of evidence. From initial forensic cell phone data recovery through analysis and reporting, every step must be documented. Any break in the chain of custody or potential alteration threatens admissibility. Ethical practitioners must adopt best practices like cryptographic hashing, write-blocking, and secure storage.
Mobile Forensics in Practice: Challenges and Case Scenarios
Scenario: Domestic Dispute and Hidden Data
Consider a domestic dispute investigation. A warrant authorizes the extraction of text messages between specific parties during a defined timeframe. During data extraction, an investigator stumbles upon unrelated messages referencing personal health issues or third parties. Ethically, the investigator must pause and assess whether to retain those messages. Unless they are clearly relevant, the messages should be redacted or excluded altogether. Failure to do so could violate privacy and lead to suppression motions.
Scenario: Organized Crime and Broad Authority
In a wide-ranging organized crime investigation, a warrant may permit the extraction of broad categories—call logs, location data, app metadata, and multimedia. The investigative team, with forensic video analysis capabilities, may encounter vast amounts of private content. Here, the oversight of a digital forensic consultant becomes vital to ensure proportional access and compliance with minimization principles, so privacy rights aren’t overwhelmed by overcollection.
Scenario: Cloud Backup and Jurisdictional Issues
A suspect’s mobile device is backed up to a cloud service in another country. The investigation team wants access to synced photos stored overseas. The domestic warrant doesn’t directly authorize foreign server access. The data forensic expert must seek international cooperation, mutual legal assistance treaties (MLATs), or separate legal orders. In the meantime, investigators cannot overreach into data stored in foreign jurisdictions.
Best Practices: Striking the Right Balance
- Obtain Specific Legal Authorization: Always acquire search warrants with clearly defined scopes and permissible categories. Avoid vague language that could allow overreach.
- Segmented Extraction & Filtering: Use techniques to limit extraction to defined time periods, keywords, apps, or file types. This helps prevent unnecessary exposure to private data.
- Use Validated Tools and Methods: Work with accredited and courtroom-accepted tools for digital forensic services to ensure data integrity and defensibility.
- Redact Irrelevant Content:After extraction, review and redact data unrelated to the investigation to respect privacy rights.
- Maintain Transparent Logs: Document every step—tool used, extraction path, filtering criteria, chain of custody—to provide accountability and defend against suppression challenges.
- Expert Peer Review: Engage a digital forensic engineer to review processes, ensuring procedural compliance and ethical discipline.
- Collaborate with Legal Counsel: Work closely with prosecutors and defense counsel to ensure warrants comply with the Fourth Amendment, ECPA, SCA, and jurisdictional limits.
- Stay Current with Law & Tech: The legal and technical landscape evolves rapidly. A digital video forensics expert must remain updated on trends, new statutes, court decisions, and encryption techniques.

Risks, Consequences & Judicial Scrutiny
When forensic professionals overstep, the consequences can be severe. A court may suppress evidence—or the entire forensic extraction—if privacy violations are found. Worse still, misconduct may lead to professional discipline or civil liability.
A judge reviewing a suppression motion will scrutinize whether the search was narrowly tailored, whether the practitioner exceeded the warrant, and whether redaction and minimization occurred. That underscores the imperative for ethical restraint.
Moreover, reputation matters. A law enforcement agency or forensic vendor that earns a reputation for invasive or sloppy mobile forensics can lose credibility, damage trust, and invite public backlash.
Emerging Trends: Privacy-First Approaches and Privacy-Preserving Forensics
As privacy awareness grows and legal standards tighten, more forensic methodologies are adopting privacy-first approaches. One such technique is targeted imaging, where only limited partitions or specific file sets are extracted, rather than a full image dump.
Another is in‑device filtering, where a tool on the device (under legal permission) preselects relevant content before extraction. Some research focuses on homomorphic encryption or secure multiparty computation in forensic settings, allowing pattern matching without fully exposing content.
Additionally, differential privacy techniques may be applied to metadata analysis, where aggregate or anonymized patterns are analyzed without revealing individual content. Still, these are nascent and must align with evidentiary rules.
In parallel, standards bodies and accreditation organizations (e.g., National Institute of Standards and Technology, forensic certifying bodies) are pushing for clear guidelines to limit privacy risk in mobile forensic operations.

This is not a mere academic debate: real lives and real justice hang in the balance. Each mobile case must be handled with a blend of technical acumen, legal awareness, and moral restraint. When done right, mobile forensics can be a powerful force for truth without trampling the very freedoms it seeks to uphold.
If your investigation demands trustworthy mobile forensics privacy issues handling, choose experts who balance privacy and evidence seamlessly.
Eclipse Forensics stands ready to provide comprehensive mobile device forensics, forensic cell phone data recovery, and other cell phone forensic services while safeguarding individual rights.
Our team includes seasoned digital forensic engineers, forensic video analysis experts, and audio forensic specialists.
Whether you need assistance in digital forensic services, video forensic services, or audio authentication services, we deliver precise, legally defensible results.
From digital forensic consultant guidance to forensic computer analyst reviews, we support law enforcement, legal teams, and private clients. Contact Eclipse Forensics today for reliable, ethical, and expert forensic solutions.