Have you ever wondered if a recorded phone call can be trusted? In a world where audio manipulation has become more accessible than ever, it’s a valid concern.
Phone call authentication is an essential process that verifies whether a recorded conversation is genuine, tampered with, or entirely fabricated. As digital evidence continues to influence court cases and investigations, the demand for audio authentication services and forensic verification is growing.
In this blog, we’ll break down how experts detect fake conversations, what forensic tools and techniques they use, and why phone call authentication plays a crucial role in modern justice.
Let’s dive into the fascinating world where technology meets truth.
Why Phone Call Authentication Matters
Recorded phone calls can serve as powerful evidence in legal disputes, criminal investigations, and even workplace conflicts. But audio evidence is only valuable if it’s proven to be authentic. In an age of deepfake technology and sophisticated audio editing tools, phone call authentication ensures that justice is based on facts, not fabrications.
Authentication not only verifies the integrity of a recording but also determines whether the voices, background noises, timestamps, and frequency ranges align with what’s expected from an unaltered recording. Without proper verification, a manipulated recording could lead to wrongful accusations or compromised investigations.
The stakes are high—especially in criminal trials or high-profile civil cases—where a single piece of audio can influence verdicts, settlements, or reputations. That’s why authentication isn’t just a technical step; it’s a safeguard for truth and fairness in any context where recorded conversations matter. For law enforcement, employers, journalists, and individuals alike, knowing that an audio file is genuine provides peace of mind and legal confidence.

The Core Process of Phone Call Authentication
Phone call authentication involves a systematic approach where forensic audio specialists evaluate recordings using scientific principles. Here’s a look at the typical steps taken:
1. Initial Assessment and Chain of Custody
Before any analysis begins, forensic experts ensure the evidence was handled correctly. Establishing a clear chain of custody is crucial to preserving the integrity of the audio file.
2. Digital File Inspection
Experts examine the format, metadata, and digital signatures of the file. They look for anomalies like inconsistent timestamps, unusual codec information, or compression artifacts that could indicate tampering.
3. Waveform and Spectral Analysis
A visual representation of the audio signal allows forensic specialists to detect unnatural changes. Spectrograms reveal frequency shifts, background inconsistencies, or cut-and-paste signs that the human ear might miss.
4. Voice Identification
In some cases, experts compare voice samples to verify speaker identity. Using biometric voice analysis and comparing pitch, tone, and cadence helps determine if the speaker is indeed who they claim to be.
5. Background Noise Evaluation
Ambient noise can serve as an authentication marker. Analyzing the consistency of background sounds like traffic, birds chirping, or a clock ticking can show if parts of the recording were spliced or modified.
6. Editing Detection
Specialized software is used to detect edits, deletions, or insertions. Discontinuities in the waveform or spectral fingerprint can highlight where manipulation occurred.
7. Report Generation and Expert Testimony
Once the analysis is complete, a forensic audio specialist compiles a detailed report. This documentation may be used in court, often accompanied by expert testimony to explain the findings.

Tools of the Trade
Forensic audio experts rely on a suite of sophisticated tools and technologies to perform their analysis. Here are a few key examples:
- Spectrogram Analysis Software: Tools like Adobe Audition, iZotope RX, and forensic-specific platforms offer high-resolution views of audio frequency and intensity.
- Voice Biometrics: Used to compare voice samples, this tech analyzes unique vocal patterns.
- Audio Editing Logs: Advanced software can generate logs to show if and when edits were made.
- Metadata Extraction Tools: Reveal hidden information embedded in digital files, such as recording time, device used, and software history.
Real-Life Applications of Phone Call Authentication
Here are some real-life applications of the phone call authentication process.
1. Criminal Investigations
In law enforcement, a recorded phone call might be the critical link in solving a case. But unless it’s authenticated, it could be challenged in court. Phone call authentication helps validate confession recordings, undercover operations, or ransom calls.
2. Corporate Disputes
Businesses rely on audio documentation during HR investigations, legal disputes, or contract disagreements. Confirming a call’s authenticity can either reinforce or refute claims made by employees or clients.
3. Domestic and Family Cases
In custody battles or divorce proceedings, recorded phone calls may be submitted as evidence. Authenticating these conversations helps protect individuals from fabricated accusations or misinformation.
4. Media and Journalism
Audio leaks can cause public uproar, but how do we know if they’re real? News agencies may consult forensic experts to validate leaked phone calls before publishing.

Challenges in Phone Call Authentication
While technology provides advanced tools, the process isn’t without its challenges:
Low-Quality Recordings:
Poor audio quality from cheap recording devices or noisy environments can make analysis difficult. In such cases, even high-end forensic tools may struggle to separate voices from interference or background noise. This can delay the authentication process or reduce the certainty of findings.
Encrypted or Proprietary Formats:
Some files are saved in uncommon or encrypted formats, requiring custom decoding tools. Extracting clean, usable data from these formats often involves technical expertise, file conversion, and sometimes even reverse engineering.
Intentional Obfuscation:
Tech-savvy individuals may intentionally manipulate recordings to avoid detection. They might layer noise, distort voice frequencies, or introduce brief silences to confuse waveform analysis. These sophisticated tactics require equally advanced forensic techniques to uncover the truth.
Legal Hurdles:
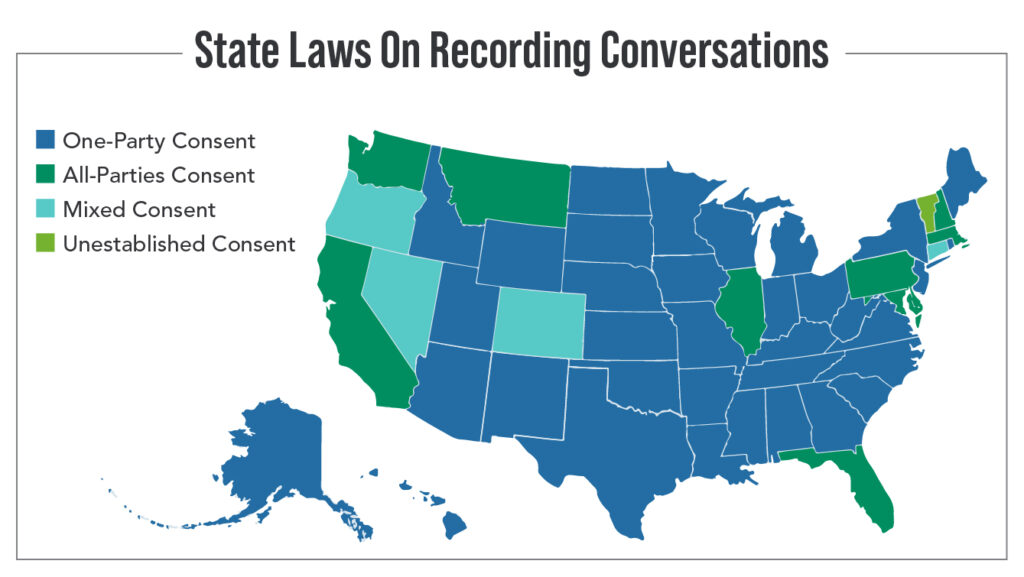
Laws governing audio recordings vary widely. In some jurisdictions, consent must be obtained from all parties before recording a conversation. If a recording is obtained illegally, it could be inadmissible in court regardless of its content or authenticity. Forensic experts must work closely with legal teams to ensure their methods and findings comply with applicable regulations.
Time Sensitivity and Data Loss:
Sometimes, critical audio files are not preserved properly or are deleted before authentication can occur. In such cases, data recovery becomes a parallel challenge, requiring a data forensic expert to retrieve lost evidence from digital storage.
These challenges highlight why phone call authentication is best handled by seasoned professionals who understand both the science and the legal implications of forensic audio analysis.
How Deepfakes Complicate the Picture
With the rise of AI-generated audio, creating entirely synthetic conversations using someone’s voice is possible. These deepfakes can be frighteningly realistic and raise new concerns about the validity of phone call evidence.
Deepfake audio uses artificial intelligence to mimic a person’s voice by training on existing voice samples. With just a few minutes of recorded speech, algorithms can generate new audio clips that sound like the real person but say things they never actually said.
This technology has grown increasingly accessible, with open-source tools available online. As a result, creating fraudulent audio is no longer limited to high-tech labs—anyone with basic software skills and a computer can produce convincing fake conversations.
What makes deepfakes particularly dangerous in legal and forensic contexts is their realism. Unlike traditional audio edits that may leave detectable signs like inconsistent background noise or mismatched frequencies, deepfakes can sound seamless. That’s why detecting them requires specialized expertise.
Forensic experts now adapt their methods to detect deepfake audio by analyzing artifacts left behind during the synthesis process. These subtle clues are often invisible to the untrained ear but can be exposed using machine learning and advanced waveform analysis.
As deepfake technology continues to evolve, so must our forensic defenses. Phone call authentication is becoming more important than ever to ensure that justice relies on truth, not digital trickery.
How Eclipse Forensics Supports Phone Call Authentication
At Eclipse Forensics, we understand how crucial phone call authentication is in today’s digital world. Our team of seasoned professionals is equipped with the latest tools and training to analyze recorded conversations and uncover the truth behind the sound.
As a leading forensic audio specialist facility, we handle each case with the highest level of care, confidentiality, and scientific rigor. Our clients include law enforcement agencies, attorneys, corporations, and private individuals who depend on us to deliver clear, factual, and court-admissible findings.
We don’t just analyze audio. As a trusted cyber forensic expert team, we also dive into digital trails, mobile device data, and surveillance videos when needed. Our data forensic experts use advanced software to reconstruct data, find hidden files, and validate metadata to support the authentication process.
If your case involves visuals, we’ve got you covered there too. Our video forensic services include frame-by-frame analysis and enhancement of visual recordings to support the integrity of both audio and video files. We also offer forensic image analysis to verify or clarify still images connected to phone call investigations.
Whether you’re dealing with a legal battle, a corporate dispute, or a personal issue, you deserve to know the truth. Our phone call authentication services are designed to reveal exactly that.
If you suspect a recording has been manipulated or need a second opinion on a critical piece of audio evidence, reach out to us.

