What if one altered file could send someone to prison—or let someone walk free? In a time when digital data serves as both evidence and alibi, the integrity of that data carries enormous weight. From emails and text messages to CCTV footage and metadata, modern legal cases rely on digital evidence more than ever before. Yet, even minor tampering can significantly alter a case’s outcome, impacting everything from bail hearings to final verdicts.
That’s where we come in. At Eclipse Forensics, we provide expert digital forensic services designed to detect manipulation, authenticate media, and support legal teams with high-stakes litigation. Whether it’s examining altered timestamps or validating surveillance footage, our work helps uphold the truth.
In this blog, we’ll explain how tampered digital evidence affects court proceedings, what the legal consequences are, how it can be detected, and why forensic video analysis and cell phone forensic services are essential to preventing wrongful convictions or acquittals.

Why Evidence Tampering Happens—And Why It Matters
Digital evidence tampering isn’t just about malicious intent. Sometimes, it’s caused by poorly handled devices, unauthorized access, or even auto-syncing software. However, the legal system rarely distinguishes between malicious and accidental alteration. If evidence can’t be authenticated, its admissibility is immediately in question.
Common Types of Evidence Tampering:
- Metadata manipulation – Changing dates or GPS coordinates in photos or videos
- File modification – Editing documents, emails, or audio recordings
- Selective deletion – Removing incriminating texts or messages
- Splicing or cutting footage – Altering video evidence to misrepresent context
- Spoofing data – Creating fake communications or digital artifacts
When evidence like this enters a courtroom, it can skew the facts, mislead the jury, and derail the case—whether civil or criminal.
Legal Implications of Altered Evidence
Now let’s talk about the big issue: what happens legally when evidence is proven to be tampered with? Whether it’s the prosecution or defense responsible, the consequences are serious and long-lasting.
1. Admissibility Issues
Judges can—and often do—throw out any evidence that appears altered or untrustworthy. Under the Federal Rules of Evidence, specifically Rule 901, evidence must be authenticated before being presented. If a digital forensic expert can’t validate a piece of evidence, it may never make it before a jury.
- Evidence may be excluded if:
- It lacks a clear chain of custody
- Metadata appears inconsistent or edited
- The source is unknown or unverifiable
- Forensic analysis reveals signs of tampering
2. Mistrials and Case Dismissals
If altered evidence is presented during a trial and the manipulation is discovered after admission, the court may declare a mistrial. This stalls proceedings, wastes judicial resources, and delays justice.
3. Perjury and Obstruction Charges
Submitting altered evidence intentionally can lead to criminal charges for the party responsible. Prosecutors, attorneys, or even witnesses can face penalties including:
- Contempt of court
- Fines
- Jail time
- Professional sanctions
The Role of a Digital Forensic Consultant in Protecting Evidence Integrity
So how can we ensure digital evidence stands up in court? That’s where digital forensic consultants step in. Our role is to review, extract, and preserve digital data without altering it, then analyze it for authenticity.
We handle:
- Forensic imaging of devices to preserve original data
- Hash validation to confirm data integrity
- Chain-of-custody documentation from collection to courtroom
- Expert testimony on findings in court
Our digital forensic services help attorneys, investigators, and courts trust that the evidence they’re relying on hasn’t been corrupted—intentionally or otherwise.
Key Tools and Techniques Used to Identify Tampering
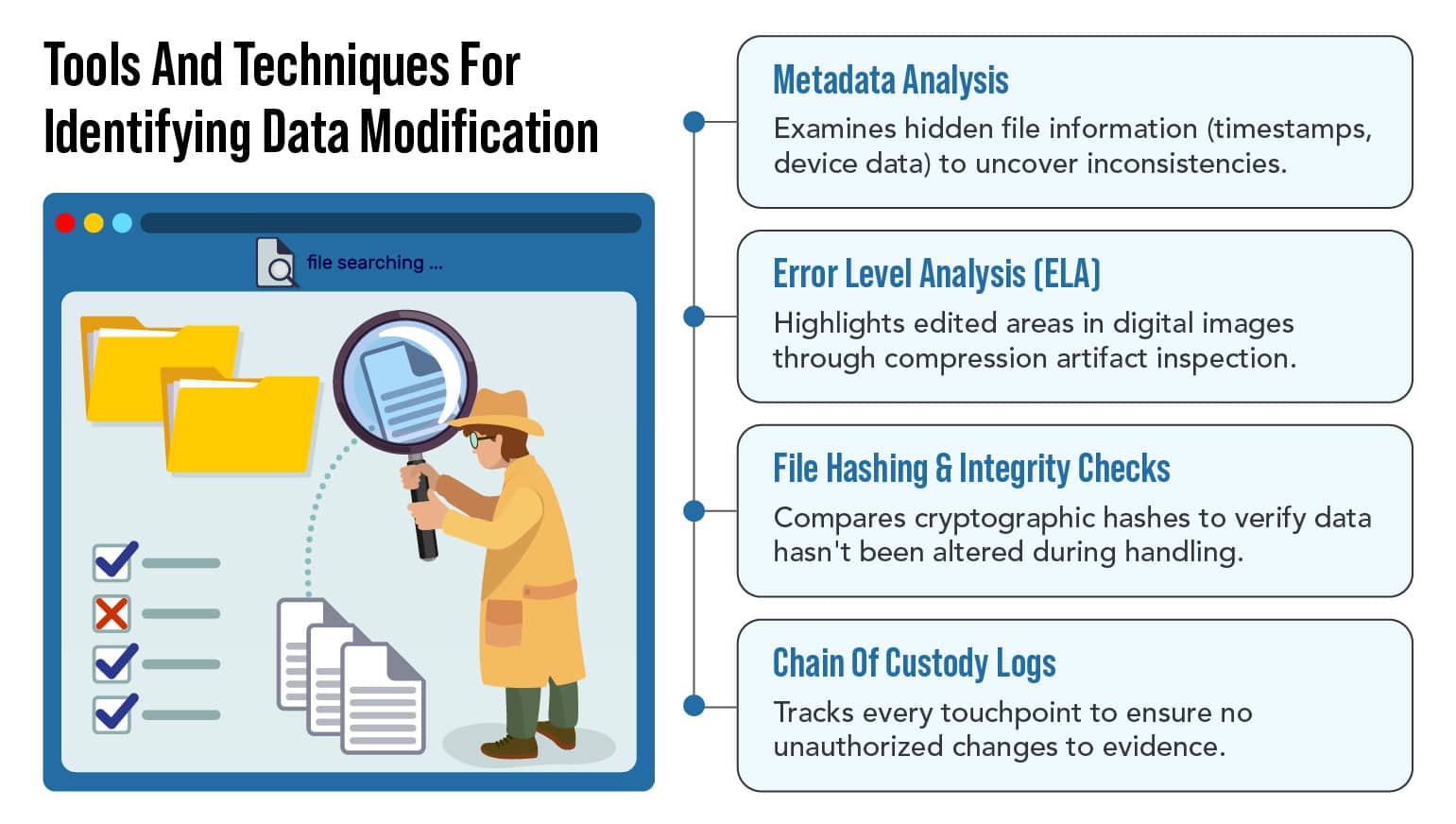
As digital forensic experts, we apply a combination of software tools and manual processes to detect even the subtlest manipulations.
Some of the most common techniques include:
- Hash matching: Any change to a file alters its hash. We verify whether the original and presented hashes match.
- EXIF metadata review: Photos often contain hidden data like location, camera model, and timestamps, which can be cross-checked.
- Hex-level analysis: Allows us to see beneath the file interface and detect manual edits.
- Forensic video analysis: Identifies splicing, frame drops, or unnatural transitions in video files.
- Deleted file recovery: Restores deleted items to assess whether selective deletion occurred.
Each step ensures that tampered evidence is flagged—and authentic data is protected.
Real-World Examples of Tampered Evidence Affecting Cases
Let’s take a look at how altered evidence has changed the trajectory of real legal battles:
Case 1: Modified Surveillance Footage
In a retail theft case, the store owner submitted video footage showing the suspect allegedly pocketing an item. However, a video forensic expert identified a break in the video’s timestamp sequence. Upon further investigation, it was revealed the footage had been edited to remove a frame showing the item being placed back. The case was dismissed.
Case 2: Falsified Text Messages
A spouse submitted a string of text messages as evidence in a custody dispute. Upon forensic review, it was discovered that the messages had been manually entered into a phone and screenshots were then taken—making them inadmissible. The court issued sanctions against the submitting party for attempting to mislead the court.
Case 3: Deleted Browser History
In a corporate espionage case, a suspect wiped his browser and file history. However, our computer forensics expert witness was able to retrieve shadow copies and system logs proving that confidential documents were accessed and downloaded. The evidence stood in court and led to a conviction.
These examples demonstrate that manipulated digital evidence isn’t just a technical issue—it can shift outcomes, destroy credibility, and even trigger criminal penalties.
How Courts Evaluate Evidence Authenticity
Courts rely heavily on the qualifications and testimony of digital forensic experts when making authenticity decisions. Judges are not technical experts, so we must explain in plain language how we verified the evidence or discovered alterations.
Key factors considered:
- Was the data extracted using accepted forensic tools?
- Was a proper chain of custody maintained?
- Were controls in place to prevent data alteration?
- Did an expert independently verify the evidence?
Being able to answer these questions is what separates admissible evidence from dismissed claims.
Why Cell Phone Forensic Services Are Becoming Essential
Mobile devices are now the primary source of evidence in many cases—civil and criminal alike. But they are also some of the easiest to manipulate. That’s why cell phone forensic services are vital.
From social media screenshots to GPS trails, call logs to deleted texts, the wealth of information on smartphones is staggering. But retrieving and authenticating that data requires skill, specialized software, and strict legal compliance.
Our work as mobile forensic specialists ensures:
- Data is extracted without altering original content
- Time-sensitive data like app usage logs are preserved
- Deleted or hidden data is recoverable and usable in court
- Forensic reports are formatted for legal admissibility
The Role of a Computer Forensics Expert Witness
Beyond analysis, we often serve as expert witnesses. That means:
- Providing sworn affidavits
- Explaining findings during deposition or trial
- Educating the court on forensic procedures
- Defending methodology under cross-examination
Our credibility can make or break a digital evidence argument. So we always ensure our work meets the highest standards of forensic science and legal admissibility.
Why Legal Teams Need Video Forensic Experts on Standby
As video becomes more common in everything from criminal trials to civil disputes, the need for forensic video analysis grows.
Whether it’s police bodycam footage, dash cams, home surveillance, or security system feeds, videos can be manipulated subtly or significantly. That’s why a video forensic expert plays a critical role in helping the court understand:
- If a video was altered
- What’s missing or edited
- How the original timeline compares to the submitted version
With tools like frame-by-frame analysis and timestamp verification, we expose inconsistencies that could otherwise go unnoticed.
So, How Can You Protect Your Case from the Dangers of Altered Evidence?
We know how damaging altered evidence can be. That’s why legal teams, businesses, and even law enforcement need trusted digital forensic services from the start.
When data authenticity is in question, acting fast makes a huge difference. Time-sensitive information can be overwritten. Devices can auto-update. Logs can vanish. Don’t wait until evidence is challenged—be proactive.

What’s at Stake If You Don’t Verify Your Evidence?
What if the one piece of evidence that could have changed everything is deemed inadmissible? What if the opposing counsel proves your data was altered, even unintentionally? What if your entire case unravels because someone tampered with a file and no one caught it?
We can help make sure that never happens.
At Eclipse Forensics, we bring decades of experience in forensic video analysis, mobile device investigations, and expert courtroom testimony. Our digital forensic consultants are trained to detect even the most subtle manipulations, and our services cover everything from cell phone forensic services to full-scale litigation support.
Whether you’re an attorney preparing for trial, a business safeguarding proprietary data, or an individual caught in a complex dispute, our digital forensic services can give you the clarity and credibility you need to move forward with confidence.
Don’t risk your case on compromised evidence. Reach out to Eclipse Forensics today and let a trusted computer forensics expert witness help preserve, validate, and defend your digital truth.

